Two courses, one common development approach
It's been a while since we've rolled out a new course. But we're pleased to announce the soft launch of two in-person live courses, both taking subsets of the curriculum of our Adversary Simulation, Detection and Counteraction (ASDC) approach.The first course is actually catered for people that wish to understand basic cybersecurity concepts, specifically pertaining to cyber incidents, breaches, and generic news reports on cybersecurity stuff. The objective is to provide demonstrations and some hands-on to demystify the black magic of generic cybersecurity processes. It is essentially ASDC (Fundamental), without most of the practical aspects (and without the certification process), and is more for appreciation.The second course is catered to address threat hunting practitioners, focusing on kickstarting the basic investigative mindset, a very rough understanding of how threat actors work, and good old "back to basics" commandline tools. Sysmon may or may not be included. Everything in a simulated environment, with simulated threat(s) and realistic users. This is squarely within the ASDC (Intermediate) scope, but this doesn't mean that the approach has to differ completely from the first course.The common denominator
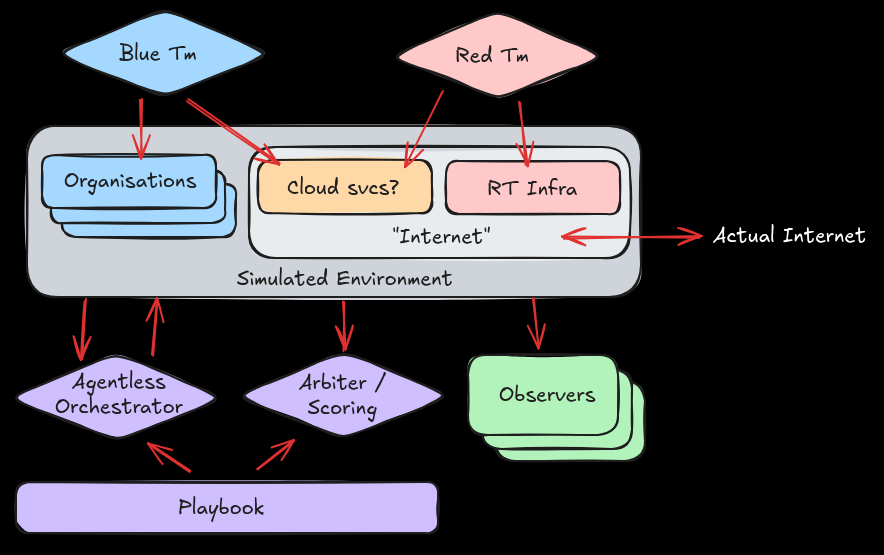
In both course setups, most decent course providers will provide a simulated environment, conducting demonstrations and practical exercises within the environment. However, the artificiality of the environment is usually the issue. It is trivial to set up an Active Directory environment, more difficult to create simulate activity in the environment, and even more difficult to simulate actual human activity without creating agents or bots on the machines to run the activity. Arguably, most customers won't demand that sort of realism, and most vendors will tell their trainees to "ignore [unrealistic daemon] for this exercise".For counterShell, we believe that real-life is always the complicating factor, and we strive to emulate real-life as much as we can. However, this is not entirely a technical exercise: it is rooted in proper learning needs analysis and manifests in learning solution design. From a personal standpoint, I used to jump into the technical aspects of a would-be solution because it's fun... only to realise that perhaps it's not the correct solution to begin with.It’s easy and fun to come up with diagrams, and possibly just as fun trying to develop a technical POC of the solution. But it’s important not to lose sight of the question that we’re trying to answer.
On one hand, I think this solution won't be too far from the "correct" approach to address both courses. However, I get the feeling that I will be fine-tuning this solution quite a bit to address learning needs of the variety of industry needs out there. Another problem is that such an approach has never been fully developed and tested in the industry yet (as far as I know). Ultimately, this leads me to believe that developing my abilities in learning solution design will help me better focus my technical abilities to address the correct issues that up-and-coming cybersecurity professionals face.Wrapping Up
In any case, counterShell is committed to providing realism through our courses and training solutions... and on that note, we have soft-launched the threat hunting course for organisations here. An individual-level course is on the way as well, just that we will likely package it together with the other ASDC modules, so stay tuned.The ASDC appreciation course is being finalised and will launch soon, and it will feature some of the realism that we're incorporating for the other courses. Just like how realism helps cybersecurity practitioners, we believe this touch of realism will help connect our learners to the material more effectively, especially at the fundamental, foundational level.