ShellGym: Reversing for Exploitation
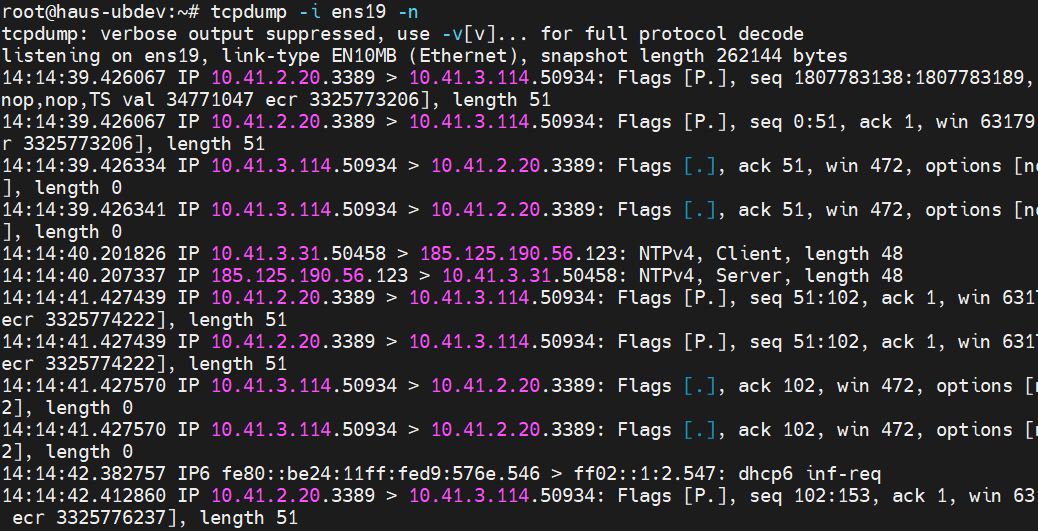
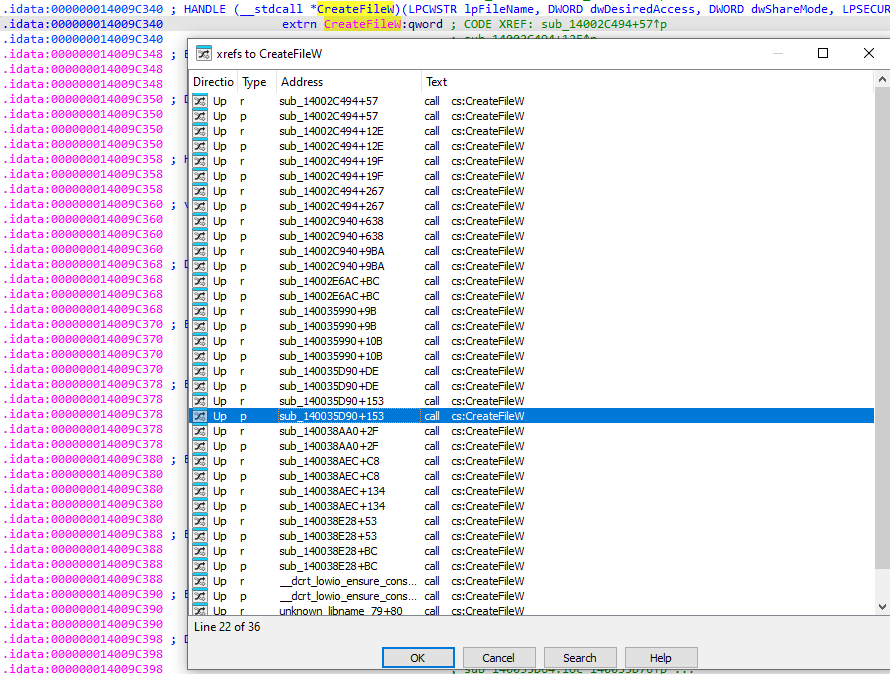
In line with the concept of using real-life examples to introduce basic reverse engineering concepts and tools, we covered a recent Winrar path traversal CVE (CVE-2025-8088) and its exploitation process, in the recent ShellGym session with Div0. Exploit POCs already exist, and detection techniques exist as well to detect the malformed rarfile containing the path traversal. Can we evade the detection with a rarfile with encrypted file names (ie, the -hp option in rar.exe)? While this is possible, the POCs no longer work, as they rely on editing an unencrypted rarfile. This short writeup just goes through the process, and our takeaways from this session.

Two courses, one common development approach
Most decent course providers will provide a simulated environment, conducting demonstrations and practical exercises within the environment. However, the artificiality of the environment is usually the issue.

ShellGym: Javascript fun and games
Occasionally, I get the comment that "manipulating client-side is not useful", because the real vulnerabilities are in the server. Mostly, that's true. However, reflecting on my own journey into cybersecurity, I found messing around with javascript from a browser perspective to be a great way to learn cybersecurity and build coding skills in general.
On vibecoding
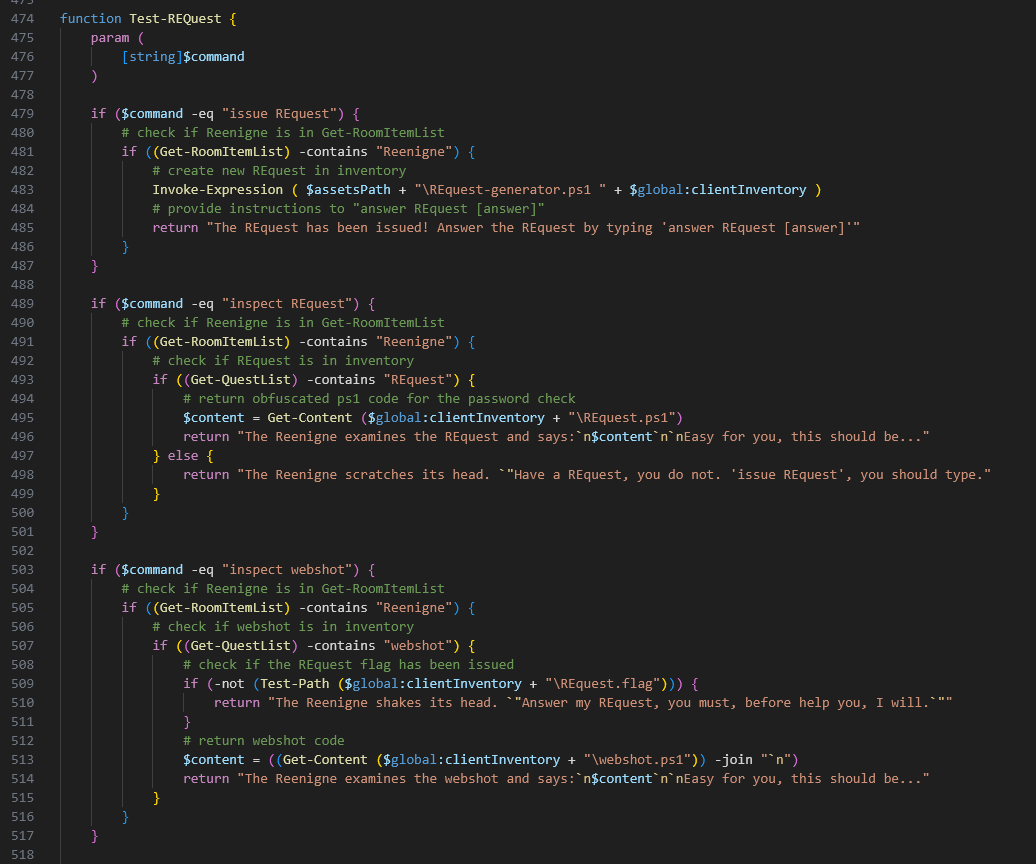
About a month ago, counterShell set up a booth at the NUS Greyhats Summit to showcase a simple CTF challenge that was crafted as a text-based RPG. Think "go caves", "get torch" sort of commands. But in the backend, it was "cd caves" and "move torch.bat %playerinventory%\torch.bat". We had 3 mini challenges as part of the overall RPG, and a meta challenge to "escape" out of the game.
The challenge was written in PowerShell, and mostly vibecoded. Before you close this tab in disgust, perhaps let me share a few observations on vibecoding that hopefully will redeem myself.

SHELLSHOCK @ SINCON 2025
counterShell conducted a SHELLSHOCK workshop at SINCON 2025, intended to cover some simple aspects of adversary simulation. As mentioned in the workshop, the reason for the name "SHELLSHOCK" was not about the actual shellshock vulnerability, but the shock you get when you realise these simple tricks can get you shell. The tricks covered in the workshop are not rocket science nor are they the product of any deep research: we believe that they can be applied by entry-level cybersecurity practitioners.

Cybersecurity by counterShell
counterShell is participating in SINCON 2025, hosting our SHELLSHOCK workshop with a sharing by our very own KK. Despite advancements in cyber defenses, breaches still occur—SHELLSHOCK equips participants with a hands-on understanding of attackers, defenders, and users by immersing them in both offensive and defensive roles within realistic Windows-based scenarios. Read our hot takes here.

SAIC Post-Course Review 2
The Security Analyst Introductory Course concluded its 3rd run on 11th April 2025, after two successful runs in March (link to blog post 1). We designed this course to cater to non-cybersecurity practitioners, and the initial feedback we got was that the course was too short and a little too advanced. This time round, we included some pre-reading material, which helped to provide a baseline for participants.

SAIC Post-Course Review 1
The Security Analyst Introductory Course concluded its 2nd run on the 14th of March 2025. We designed this course to cater to non-cybersecurity practitioners, aimed at imparting the skills to allow them to analyse the cybersecurity layout of an organisation from a Blue Team's perspective and from a threat actor's perspective. Nearly all of the participants were not from technical backgrounds, but were working with cybersecurity professionals to perform cybersecurity evaluations.
