ShellGym: Javascript fun and games
Client-side stuff is not dead - exploring gamification beyond CTFs
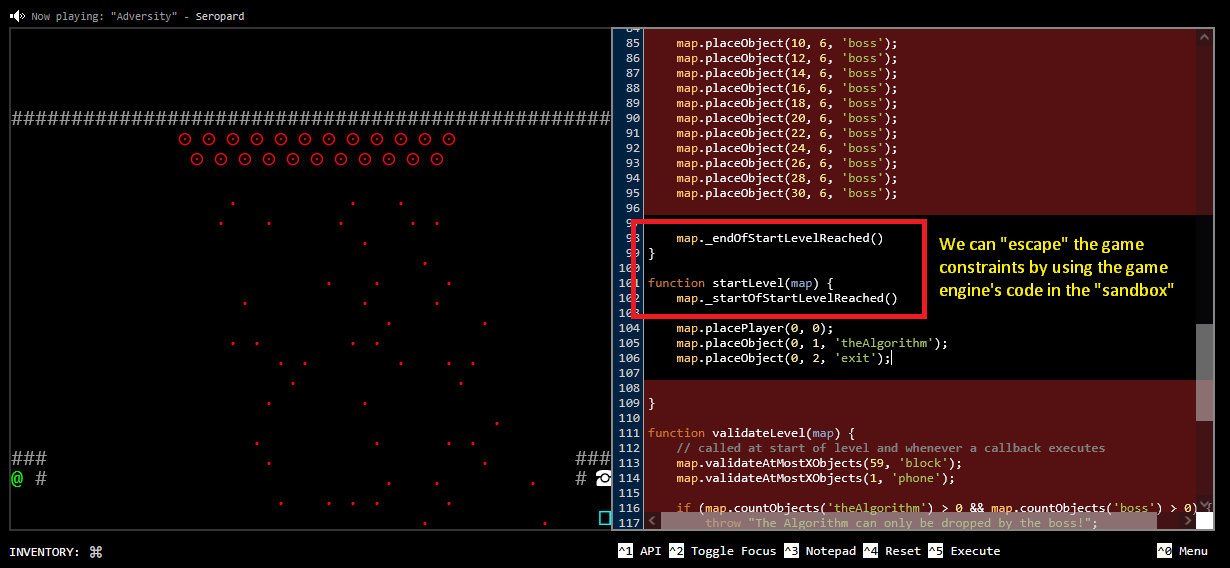
We conducted ShellGym over the weekend, and we hope this was a fruitful session for all who attended. This time round, we had many newcomers to cybersecurity, along with a few practitioners (and one or two particularly seasoned experts). The session was on web pentesting without tools, just utilising the native browser and CLI tools to get things done. We also worked a bit with javascript and client-side work.Occasionally, I get the comment that "manipulating client-side is not useful", because the real vulnerabilities are in the server. Mostly, that's true. However, reflecting on my own journey into cybersecurity, I found messing around with javascript from a browser perspective to be a great way to learn cybersecurity and build coding skills in general. Take this game for example: https://untrustedgame.com/. On one hand, we can play the game normally and learn quite a bit from it. The game also attempts to infuse the "hacker mentality" by forcing our code to work within the constraints of the game. Much like a sandbox. On the other hand, we can attempt to escape this sandbox:The layout of the game is represented by the JS code on the right. You can only add code in the black segment, so by rights, the red segments cannot be modified or tampered with. Or can it? Looking through the game code and performing some debugging shows how the game tries to parse the user generated code, inserting some markers to denote the start and end of the level.
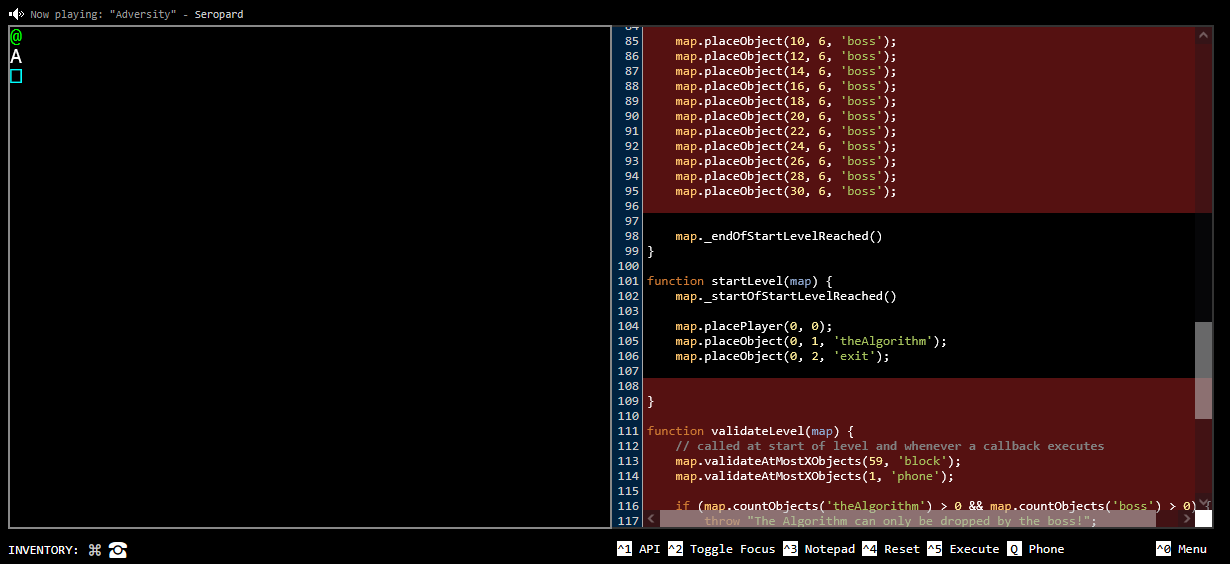
The result of executing the code. The entire level has been bypassed and replaced with our own constructed level. We can apply this “hack” to almost all the other levels in the game to escape the imposed constraints.
Part of gamification is breaking the game. Meta-gamification?
Escaping the game constraints requires the ability to trace someone else's program execution, debug and understand code (in this case, javascript), which is a skill that's very applicable to cybersecurity. And it's fun. From the perspective of the participants of ShellGym, the exercise (hopefully) opened up a new, fun and educational avenue to learn cybersecurity - through gamification beyond CTFs and vulnerable boxes. Actually, I'd argue that in the pre-CTF era, the mentality of game hacking and finding ways to cheat a system probably sparked the interest of the older cybersecurity professionals today, a view that is shared with many of my colleagues (and ex colleagues) from this field. From industry literature, the ability to think out of the box, challenge assumptions, figure out how things actually work, and attempt to reproduce unexpected behaviour (eg, glitches) in a game (or other systems), are hallmarks of a cybersecurity professional. It was certainly heartening to see our participants realising this for themselves as they replicated the thought process and exploitation process.ShellGym in session!
The Future of ShellGym
What's next from here? The next few ShellGym sessions will incorporate more of these sorts of open-ended "games" and challenges, contextualised to the content we're covering in the session. In the next session in August, I intend to cover reverse engineering, but apply it to more real-life scenarios, where it is more open-ended and there are no "flags". This would probably allow me to adopt a more personalised learning approach, where there are multiple ways to achieve an objective, and it is up to the learner to identify a viable approach and work with it.I picked up reverse engineering by doing CTFs and figuring things out for myself, and I used to think that this was the best approach. However, after this ShellGym session, I intend to explore using a set of at least three illustrative real-life examples to demonstrate the mental process of reverse engineering. And yes, I intend to show how some of these processes can be done without specialised tools. To supplement these examples (and to test out my new approach of moving away from CTFs), I will also develop a more complex program (probably a game?) to reinforce the reversing and hacking concepts. :) On a more long-term front, I intend to make ShellGym a regular monthly session, with our friends at Div0 or otherwise. These monthly sessions will cover topics, mainly at the foundational level, in order to demystify the "black magic" of cybersecurity. Besides ShellGym, I'm also aiming to start a more "advanced" session for seasoned practitioners to cover deeper technical topics, particularly those I'm crafting for my flagship courses. Stay tuned for updates...